Classification of computer networks by scale
According to the Table 5 above, the networks can be classified into six classes abbreviated as PAN, LAN, MAN and GAN.
Personal Area Network (PAN)
A personal area network (PAN) is a computer network that will be useful in communicating computerizes devices such as telephones and PDAs. Mostly, the PAN is communicated through wireless network technologies such as Wireless USB, Bluetooth, Z-Wave, and IrDA. You may use PANs to communicate among the personal devices or you may connect even to higher level networks or to the internet.

Figure 10- Personal Area Network
Local Area Network (LAN)
A local area network (LAN) is a computer network covering a small geographic area, like a home, office, or group of buildings. Ex: a school (See Figure 11 below). The defining characteristics of LANs, in contrast to Wide Area Networks (WANs), include their much higher data transfer rates, smaller geographic range, and lack of a need for leased telecommunication lines. LANs can be small, linking as few as three computers, but often link hundreds of computers used by thousands of people. The development of standard networking protocols and media has resulted in worldwide propagation of LANs throughout business and educational organizations. The Figure 11 below shows a LAN consisting of six computers/work stations.
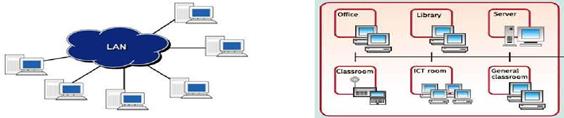
Figure 11- Local Area Network (LAN) Figure 12- LAN in a School
Wide Area Network (WAN)
Wide Area Network is defined as a group of computers and network devices connected across large physical areas such as states or countries. Computers connected to a Wide Area Network are often connected through the telephone system. They can also be connected through leased lines or satellites. One may define a WAN as a collection of several LANs as depicted in Figure 13 below.
The largest WAN in existence is the Internet. (You will learn about Internet in a coming section).

Figure 13- Wide Area Network
Metropolitan Area Network (MAN)
MAN is a network that interconnect users with computer resources in a geographic area or region larger than that covered by a local area network (LAN) but smaller than the area covered by wide area network (WAN). Further a MAN is a network that connects two or more Local Area Networks or Campus Area Networks together but does not extend beyond the boundaries of the immediate town, city, or metropolitan area. See Figures 14,15 below for a typical set up of a MAN.
|
|
|

Figure 14- Metropolitan Area Network (MAN)

Figure 15- LAN, MAN, and WAN
Classifications of networks based on the topology
Network Topology is the schematic description how the arrangement of the network is including the nodes, connecting lines, and other devices. As per the above Table 7, the main network topologies are listed below.
- Bus
- Star
- Ring
- Mesh
- Tree/Hierarchical
Deep discussions on the topologies are beyond the level of this course unit. However, brief descriptions on each topology and images of them are given below.
Bus Topology
Bus networks (not to be confused with the system bus of a computer) use a common backbone to connect all devices. A single cable, the backbone, functions as a shared communication medium that devices attach or tap into with an interface connector. A device wanting to communicate with another device on the network sends a broadcast message onto the wire that all other devices see, but only the intended recipient actually accepts and processes the message.

Figure 16- Bus topology
Star Topology
Many home networks use the star topology. A star network features a central connection point called a "hub node" that may be a network hub, switch or router. Devices typically connect to the hub with Unshielded Twisted Pair (UTP) Ethernet.
Compared to the bus topology, a star network generally requires more cable, but a failure in any star network cable will only take down one computer's network access and not the entire LAN. (If the hub fails, however the entire network also fails.)
Ring Topology
In a ring network, every device has exactly two neighbors for communication purposes. All messages travel through a ring in the same direction (either "clockwise" or "counterclockwise"). A failure in any cable or device breaks the loop and can take down the entire network.

Figure 17- Star topology
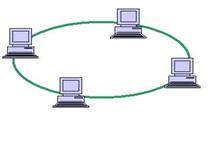
Figure 18- Ring topology
To implement a ring network, one typically uses FDDI, SONET, or Token Ring technology. Ring topologies are found in some office buildings or school campuses.
|
|
|
Mesh Topology
Mesh topologies involve the concept of routes. Unlike each of the previous topologies, messages sent on a mesh network can take any of several possible paths from source to destination. (Recall that even in a ring, although two cable paths exist, messages can only travel in one direction.) Some WANs, most notably the Internet, employ mesh routing.
A mesh network in which every device connects to every other is called a full mesh. As shown in the illustration below, partial mesh networks also exist in which some devices connect only indirectly to others.

Figure 19- Mesh topology
Tree Topology
Tree topologies integrate multiple star topologies together onto a bus. In its simplest form, only hub devices connect directly to the tree bus and each hub functions as the root of a tree of devices. This bus/star hybrid approach supports future expandability of the network much better than a bus (limited in the number of devices due to the broadcast traffic it generates) or a star (limited by the number of hub connection points) alone.

Figure 20- Tree topology
The Internet
As you are already aware, the Internet is the largest WAN in existence (See Figure 21 below). It is a network of networks that consists of millions of private, public, academic, business, and government networks, of local to global scope, that are linked by a broad array of electronic, wireless and optical networking technologies. The Internet carries an extensive range of information resources and services, such as the inter-linked hypertext documents of the World Wide Web (WWW) and the infrastructure to support email.
With the dramatic rise in demand for connectivity, the Internet has become a communications highway for millions of users. The Internet was initially restricted to military and academic institutions, but now it is a full-fledged conduit for any and all forms of information and commerce. Internet websites now provide personal, educational, political and economic resources to every corner of the planet.

|
|
|
Figure 21- Internet: the largest WAN in existence
Configuring a DHCP Server
To configure a DHCP server, you must create the dhcpd.conf configuration file in the /etc/ directory. A sample file can be found at /usr/share/doc/dhcp-<version>/dhcpd.conf.sample.
DHCP also uses the file /var/lib/dhcpd/dhcpd.leases to store the client lease database.
Configuration File
The first step in configuring a DHCP server is to create the configuration file that stores the network information for the clients.Use this file to declare options and global options for client systems.
The configuration file can contain extra tabs or blank lines for easier formatting. Keywords are case-insensitive and lines beginning with a hash mark (#) are considered comments.
Two DNS update schemes are currently implemented — the ad-hoc DNS update mode and the interim DHCP-DNS interaction draft update mode. If and when these two are accepted as part of the Internet Engineering Task Force (IETF) standards process, there will be a third mode — the standard DNS update method. You must configure the DNS server for compatibility with these schemes. Version 3.0b2pl11 and previous versions used the ad-hoc mode; however, it has been deprecated. To keep the same behavior, add the following line to the top of the configuration file:
ddns-update-style ad-hoc;
To use the recommended mode, add the following line to the top of the configuration file:
ddns-update-style interim;
Refer to the dhcpd.conf man page for details about the different modes.
There are two types of statements in the configuration file:
· Parameters — State how to perform a task, whether to perform a task, or what network configuration options to send to the client.
· Declarations — Describe the topology of the network, describe the clients, provide addresses for the clients, or apply a group of parameters to a group of declarations.
The parameters that start with the keyword option are reffered to as options. These options control DHCP options; whereas, parameters configure values that are not optional or control how the DHCP server behaves.
Parameters (including options) declared before a section enclosed in curly brackets ({ }) are considered global parameters. Global parameters apply to all the sections below it.
|
|
|
Important
If the configuration file is changed, the changes do not take effect until the DHCP daemon is restarted with the command service dhcpd restart.
Tip
Instead of changing a DHCP configuration file and restarting the service each time, using the omshell command provides an interactive way to connect to, query, and change the configuration of a DHCP server. By using omshell, all changes can be made while the server is running. For more information on omshell, refer to the omshell man page.
Additionally, a subnet can be declared, a subnet declaration must be included for every subnet in the network. If it is not, the DHCP server fails to start.
In this example, there are global options for every DHCP client in the subnet and a range declared. Clients are assigned an IP address within the range.
Lease Database
On the DHCP server, the file /var/lib/dhcpd/dhcpd.leases stores the DHCP client lease database. Do not change this file. DHCP lease information for each recently assigned IP address is automatically stored in the lease database. The information includes the length of the lease, to whom the IP address has been assigned, the start and end dates for the lease, and the MAC address of the network interface card that was used to retrieve the lease.
All times in the lease database are in Coordinated Universal Time (UTC), not local time.
The lease database is recreated from time to time so that it is not too large. First, all known leases are saved in a temporary lease database. The dhcpd.leases file is renamed dhcpd.leases~ and the temporary lease database is written to dhcpd.leases.
The DHCP daemon could be killed or the system could crash after the lease database has been renamed to the backup file but before the new file has been written. If this happens, the dhcpd.leases file does not exist, but it is required to start the service. Do not create a new lease file. If you do, all old leases are lost which causes many problems. The correct solution is to rename the dhcpd.leases~ backup file to dhcpd.leases and then start the daemon.
Starting and Stopping the Server
Important
When the DHCP server is started for the first time, it fails unless the dhcpd.leases file exists. Use the command touch /var/lib/dhcpd/dhcpd.leasesto create the file if it does not exist.4/p>
If the same server is also running BIND as a DNS server, this step is not necessary, as starting the named service automatically checks for a dhcpd.leasesfile.
To start the DHCP service, use the command /sbin/service dhcpd start. To stop the DHCP server, use the command /sbin/service dhcpd stop.
If more than one network interface is attached to the system, but the DHCP server should only be started on one of the interfaces, configure the DHCP server to start only on that device. In /etc/sysconfig/dhcpd, add the name of the interface to the list of DHCPDARGS:
# Command line options here DHCPDARGS=eth0
This is useful for a firewall machine with two network cards. One network card can be configured as a DHCP client to retrieve an IP address to the Internet. The other network card can be used as a DHCP server for the internal network behind the firewall. Specifying only the network card connected to the internal network makes the system more secure because users can not connect to the daemon via the Internet.
Other command line options that can be specified in /etc/sysconfig/dhcpd include:
· -p <portnum> — Specifies the UDP port number on which dhcpd should listen.
· -f — Runs the daemon as a foreground process. This is mostly used for debugging.
· -d — Logs the DHCP server daemon to the standard error descriptor. This is mostly used for debugging. If this is not specified, the log is written to /var/log/messages.
· -cf <filename> — Specifies the location of the configuration file. The default location is /etc/dhcpd.conf.
· -lf <filename> — Specifies the location of the lease database file. If a lease database file already exists, it is very important that the same file be used every time the DHCP server is started. It is strongly recommended that this option only be used for debugging purposes on non-production machines. The default location is /var/lib/dhcpd/dhcpd.leases.
· -q — Do not print the entire copyright message when starting the daemon.
4.Telecommunication technologies.
Telecommunications involves the transmission over long distances of all forms of information between computers various types of communication lines. By definition, to ensure prompt and accessible exchange of information files is necessary, that users had access to the Internet and software for data processing. All modern telecommunication technologies based on the use of networks.
Network resources are divided into these types:
• Hardware (servers);
• Software (provides reception, transmission and processing of information);
• Information (storage of different arrays of information).
There are several services, or types of services that are provided to consumers on the Internet. For their correct use is necessary to have two computers, one of them is a workstation user, and the second - the server is the source of network resources. The work of all services based on the use of application protocols that specify a list of rules to which all companies to ensure the compatibility of hardware and software. Also the data transfer is based on a client-server program, which involves client requesting services from the server.
The Internet can provide the following services:
• Telecommunication (messaging, information of various types and sizes, teleconference, etc.);
• Information (search for information in any format that the user interests);
• Consulting (training and advice on any matters relating to the use of public resources);
• Technical services (installation and testing of hardware and software);
• Commercial (all commercial activities on the Internet);
• On-line communication between subscribers;
• Placement of advertisements on various websites, social networks and other sites;
• Cellular and mobile communications.
The introduction of telecommunication technologies in different spheres of life
Initially telecommunication technologies conceived for uninterrupted messaging at a great distance. The uniqueness of the network was that it could properly function even after damage to its parts. Internet invented for military purposes, but it was leaked to a wide range of users and has been used successfully in many spheres of activity. With the help of scientists, students and professionals of different professions quick access to information in any format could facilitate its work. Search essential data in minutes, and the software provides them with the correct treatment. The opportunity to keep track of all the processes of personnel and execution of orders in remote access for executives, which greatly increased the productivity of labor.
Questions:
1. Why do we need to connect computers?
2. What is a computer network?
3. Briefly describe the following network components.
4. a. Client b. Server c. Hub d. Router
5. What are the differences between a Hub and a Switch?
6. How do we use a MODEM?
7. Describe the following categories of networks briefly
8. a. PAN b. LAN c. WAN d. MAN
9. Explain the classifications of networks according to the topology.
10. What does it mean Internet and Intranet? Why is it important to use intranet than internet?
11. What is the most suitable connection method for the following;
a. Computers within a laboratory.
b. Connect two computer laboratories.
References
1. June J. Parsons and Dan Oja, New Perspectives on Computer Concepts 16th Edition - Comprehensive, Thomson Course Technology, a division of Thomson Learning, Inc Cambridge, MA, COPYRIGHT © 2014.
2. Lorenzo Cantoni (University of Lugano, Switzerland) James A. Danowski (University of Illinois at Chicago, IL, USA) Communication and Technology, 576 pages.
3. Craig Van Slyke Information Communication Technologies: Concepts, Methodologies, Tools, and Applications (6 Volumes). ISBN13: 9781599049496, 2008, Pages: 4288
4. Utelbaeva A.K.,Utelbaeva A.K. Study guide for lectures on discipline “Computer science”, Shimkent 2008, 84 pages.
Lecture №8. Cybersafety.
Purpose:Have an idea aboute-business ande-government.
Plan:1.Security risks of information and their classification. Industry of cybersafety. Cybersafety and control of the Internet.
2.Malicious applications. Measures and means of information protection.
3.Standards and specifications in information security field. The acts of the Republic of Kazakhstan governing legal relations in the sphere of information security.
4.Digital signature. Encoding.
1.Security risks of information and their classification. Industry of cybersafety. Cybersafety and control of the Internet.
One of the main aspects of the problem of security automated system (AS) is the identification, analysis and classification of possible threats to specific speakers. A list of the most significant threats, assess their likelihood and model of the attacker are basic information for an optimal protection.
Information Security Risk - a set of conditions and factors that create a potential or actual violation of the existing danger of information security. AS security threats - it is an opportunity to influence the implementation of the information processed in the AS, which leads to a breach of confidentiality, integrity or availability of information, as well as the opportunity to influence the AC components, leading to their loss, destruction or failure of the operation.
threats to the security of information source - a subject that is a direct cause of a threat of safety information
The main sources of security breaches are in AS:• accidents and disasters (fire, earthquake, hurricane, flood, etc.);• faults and failures of hardware;• design and development component error AC (software and data processing technology, hardware, etc.);
• Operating error;• deliberate actions of violators.
There are many criteria for classifying threats. Consider the most common ones.
1. The nature of the origin: natural and artificial Natural threats - a threat caused by exposure to the AS and its objective elements of natural physical processes or natural phenomena, independent of man. In turn, artificial threat - a threat to the AS, caused by human activities.
2. The degree of motivation: unintentional (accidental) and intentional. The first related to the different kinds of errors - in the design of the AS, in the software, human error when working with the AS and etc. The second group is related to the self-serving, and other ideological goals of people, in this case, the intruders. The reason may be to obtain material gain, revenge, moral beliefs, and so forth.
3. The position in relation to controlled areas: internal and external threats. As an example, external threats can be to intercept data transmitted over the network or through a leak PEMIN. The internal threats include theft of media with confidential information, damage to equipment, the use of various types of bookmarks.
4. The degree of impact on AS: passive and active. Passive threats - threats that do not violate the composition and the normal operation of the AS. Example - copying of confidential information leakage through technical channels of leakage, eavesdropping, etc. Active threat, respectively, disrupts the normal functioning of the AS, its structure or composition.
5. The mean infringed property information - confidentiality, availability, integrity.
6. The type of system, which is aimed threat: a system based on a stand-alone workstation and system having a connection to the PSTN.
7. The method of realization: unauthorized access (including random) to protected information, a special effect on the information, technical information leakage through leak paths.
2.Malicious applications. Measures and means of information protection.
Malicious program (in the jargon of the anti-virus services, "malware", English malware, malicious software -. «Malicious software") - any software designed to gain unauthorized access to computing resources most computer or information stored on the computer, with the purpose of unauthorized owner use computer resources or damage (damage) owner information, and / or the owner of a computer and / or the owner of the computer network by copying, distortion, deletion or substitution of information.
| Types of viruses and malware | Description |
| joke Program | joke Program - it is a virus-like program that usually changes the appearance of elements on a computer screen. |
| "Trojan horse" | Trojan horse - is a executable program that does not replicate itself, and being introduced into the system for the performance of potentially dangerous actions, such as opening ports for hackers to access. This program often uses ports "Trojan horses" to gain access to the system. An example of a Trojan horse program can serve as asserting that it saves your computer from viruses when it actually introduces them into the system. |
| Virus | Virus - a program that can reproduce itself. For this purpose, the virus has been attached to any program. As a result, it will be automatically executed during starting of the program. Boot virus: A type of virus that infects partition or disk boot sector The malicious Java code: platform-independent virus code written in the Java language, or embedded in a Java application. A macro virus: a kind of virus, written as a macro for a specific application and often embedded in the document Viruses VBScript, JavaScript or HTML: viruses that are on Web pages and downloaded through a browser Worm: self-contained program (or set of programs) that can spread copies of itself or segments to other computers, often through email |
| The test virus | Test virus - it is an inactive file, which is detected by the antivirus program. Test viruses (such as the EICAR test script) are used to verify the correct operation of the anti-virus. |
| Packer | Packer - is compressed and / or encrypted executable for Windows or Linux, you are often a "Trojan horse". Compress executable packer difficult to determine the antivirus software. |
| Probable virus / malware | This category of viruses and malware are suspicious files with some signs of a virus or malware. For details about probable virus or malware, see the following page of the online encyclopedia viruses Trend Micro.: http://www.trendmicro.com/vinfo/emea/virusencyclo/default.asp |
| Other | The category "Other" get viruses and malware that are not related to any of the types listed above. |
Table 9- Types of viruses
Measures and means of information protection.
Information security is a confrontation of information security specialists and hackers. The attacker - a subject who illegally trying to obtain, modify or destroy data of legitimate users.
Data protection is slaboformalizuemymi task, that is, has no formal methods of solution, and is characterized as follows:• a large number of factors influencing the construction of effective protection;• lack of accurate baseline data input; • lack of mathematical methods for optimal results at the aggregate source data.
Confidentiality, integrity and availability are the three most important properties of the information in the framework of its safety:
• confidentiality of information - the state of the information in which access to it is carried out only entities that have a right to it;• integrity of the information - the state of the information for which there is no any change in any change is only intentionally subjects have a right to it;• the availability of information - the state of the information in which entities with access rights can sell them freely
Among these types of protection are the basic legal, organizational and technical protection of information.Legal protection - protection of information by legal methods, including the development of legislative and regulatory documents (acts) that regulate subjects regarding the protection of information, the use of these documents (acts), as well as supervision and control over their execution
For legal protection measures include the RК laws, decrees and other legal acts. At the legislative level, there is regulation of the rules for handling the information are determined participants of information relations, their rights and duties as well as liability in the event of breaches of the law. In some way measures of the group may include prophylactic. Their main function is to prevent potential intruders, because in most cases it is the fear of punishment stops from committing crimes. The advantages of legal protections is their versatility in terms of application to all illegal methods of information extraction. Moreover, in some cases, they are only applicable, such as in the protection of copyright in case of illegal replication.
For moral and ethical measures include standards of conduct established in the society. In some cases, they can be made in writing, such as charter or code of honor of the organization. Compliance with ethical standards is not mandatory, and is more of a preventive nature.
Organizational security measures - organizational measures designed to regulate the functioning of information systems, staff performance, users interact with the system. Among the basic organizational information protection measures can be identified as follows:
• Formation of a security policy;• The regulation of access to premises;
• Regulation of access of employees to use resources information system and others.
• Determination of liability in the event of non-compliance with information security requirements.
Organizational measures alone can not solve the security problem. They should work in conjunction with physical and technical means of information protection in the definition of the actions of people.
Physical protection is a set of tools that prevent physical penetration of a potential intruder in the monitored area. They may be mechanical, electro-mechanical or electronic devices of various types. Most often, it is with the construction of the physical protection of security begins in the organization, including the information.
The last and most extensive in its composition echelon protection system is the technical protection of information. It is this type of protection is dedicated to this course.
Technical protection of information - data protection is to ensure nekriptograficheskimi methods of safety information (data) to be protection in accordance with applicable law, the application of technical, software and software and hardware. It is important to note that technical protection - is not only a protection against leakage of information through technical channels of leakage, but also protection against unauthorized access from the mathematical effects, malware, etc. The objects of technical protection of information can be:
• information of the object;• Information system;• resources information system;• Information Technology;• software;• communication network.
We proceed to the review of the standards and specifications of two different types:
3.Standards and specifications in information security field. The acts of the Republic of Kazakhstan governing legal relations in the sphere of information security.
LAW OF THE REPUBLIC OF KAZAKHSTANOn National Security of the Republic of Kazakhstan (With amendments and additions as 26.07.2016 ) Article 4. Types of National Security
5) information security - the state of protection of information space of the Republic of Kazakhstan, as well as the rights and interests of man and citizen, society and the state in the information sphere of the real and potential threats, which provides a sustainable development of the country's independence and information.
4.Digital signature. Encoding.
1. What is a digital signature? Digital signature - is the resulting cryptographic (encryption) transformation of information using a private key signature props electronic document designed to protect the document from forgery, as well as from unauthorized changes. In fact, the electronic signature - a full, having the same legal effect as handwritten signature analogue, bonded stamp.
2. Why use digital signature? The purpose of digital signature is authentication information, ie protection of transmitted information, the participants of information exchange for guarantees of their authenticity. EDS system requires that every user has a private key that is used to generate the signature, and the corresponding public key for checking signatures and distributed to a certain circle of users in the system of information exchange.
From a practical point of view of electronic signature is used in electronic document management systems, and for participation in electronic auctions.
Three important concepts in encryption.
Private and public keys. One of the most important concepts in the encryption - key. The common encryption schemes have a private key that is kept secret on your computer and allows you to read messages addressed to you. Since you can also put the private key to send messages is protected against forgery digital signature. The public key - the file that you can share with others or publish. It allows people to share with you encrypted messages and to verify your signature. Private and public key - pair. They are like two halves of a stone, two exactly suited to each other, but dissimilar parts.
Safety Certifications. Another very important concept - a security certificate. The web browser on your computer can establish an encrypted connection with websites via HTTPS. In such cases, the browser verifies the certificate by checking public keys of domain names (eg, www.google.com, www.amazon.com and ssd.eff.org). Using Certificates - one way to confirm the authenticity of your existing public key person or a website, so you can securely exchange information with him.
The network from time to time you will see a message about a security certificate error. As a rule, the reason is to try the hotel or an Internet cafe, where you are, "open" your encrypted data exchange with the website. In addition, this error often occurs because of bureaucratic problems in the certificate system. But sometimes it occurs when you try to hacker thief, police authority or the security services to crack your encrypted connection.
Unfortunately, it is extremely difficult to establish the true cause. Therefore, when a security certificate error can not take exception to websites where you have an account or where you get very important information.
Prints keys.
The word "print" in the field of computer security can mean many different things. One of the options - "print key": a sequence of characters, such as 342e 2309 bd20 0912 ff10 6c63 2192 1928. The print key allows you to securely authenticate the private key used by anyone on the Internet. If the test print is passed, more likely that the other person is really who he claims to be. This method is not perfect: the attacker can use the same print, copy.
Questions:
1. What are the threats to information security and their classification?
2. What is cyber security industry?
3. What are there measures and the protection of the media?
4. Standards and information security specifications.
5. When is founded a law on information security?
6. What is a Digital Signature?
References
1. June J. Parsons and Dan Oja, New Perspectives on Computer Concepts 16th Edition - Comprehensive, Thomson Course Technology, a division of Thomson Learning, Inc Cambridge, MA, COPYRIGHT © 2014.
2. Lorenzo Cantoni (University of Lugano, Switzerland) James A. Danowski (University of Illinois at Chicago, IL, USA) Communication and Technology, 576 pages.
3. Craig Van Slyke Information Communication Technologies: Concepts, Methodologies, Tools, and Applications (6 Volumes). ISBN13: 9781599049496, 2008, Pages: 4288
4. Utelbaeva A.K.,Utelbaeva A.K. Study guide for lectures on discipline “Computer science”, Shimkent 2008, 84 pages.
Lecture №9. Internet technologies.
Purpose: іntroduce Internet to the student, to provide an introduction to the e-mail.
Plan:
1. Basic concepts Internet. The universal identifier of resources (URI), its assignment and components.Service DNS.
2. Web technologies: HTTP, DHTML, CSS, and JavaScript.
3. E-mail. Message format.
4. SMTP, POP3, IMAP protocols.
1. Basic concepts Internet. The universal identifier of resources (URI), its assignment and components.Service DNS.
A URL (Uniform Resource Locator) is a form of URI and is a standardized naming convention for addressing documents accessible over the Internet and Intranet. An example of a URL is http://www.computerhope.com, which is the URL for the Computer Hope website.
Overview of a URL
Below is additional information about each of the sections of the http URL for this page.

http://
The "http" stands for HyperText Transfer Protocol and is what enables the browser to know what protocol it is going to use to access the information specified in the domain. After the http is the colon( : ) and two forward slashes ( //) that separate the protocol from the remainder of the URL.
www.
Next, www.stands for World Wide Web and is used to distinguish the content. This portion of the URL is not required and many times can be left out. For example, typing "http://computerhope.com" would still get you to the Computer Hope web page. This portion of the address can also be substituted for an important sub page known as a subdomain. For example, http://support.computerhope.com forwards you to the main help section of Computer Hope.
computerhope.com
Next, computerhope.com is the domain name for the website. The last portion of the domain is known as the "domain suffix", or TLD, and is used to identify the type or location of the website. There are dozens of other domain suffixes available. To get a domain, you would register the name through a domain registrar.
/jargon/u/
Next, the "jargon" and "u" portions of the above URL are the directories of where on the server the web page is located. In this example, the web page is two directories deep, so if you were trying to find the file on the server, it would be in the /public_html/jargon/u directory. With most servers, the public_html directory is the default directory containing the HTML files.
url.htm
Finally, url.htm is the actual web page on the domain you're viewing. The trailing .htm is the file extension of the web page that indicates the file is an HTML file. Other common file extensions on the Internet include .html, .php, .asp, .cgi, .xml, .jpg, and .gif. Each of these file extensions performs a different function, just like all the different types of files on your computer.
The structure of the URL is shown in the figure below.

Figure 22: Structure of the URL
There are several domains available in the web such as:
edu = education institute
com = commercial enterprise
gov = government
org = organization
net = network provider
mil = military
2. Web technologies: HTTP, DHTML, CSS, and JavaScript.
Internet Protocols
| Internet | Refersto | Description | Internet |
| Protocol | Services | ||
| SMTP | SimpleMailTransfer | A protocol for sending e- | |
| Protocol | mail messages between | ||
| servers | |||
| POP3 | PostOfficeProtocol | Used by local e-mail clients to | |
| version 3 | retrieve e-mail from a remote | ||
| server over a TCP/IP | |||
| connection | |||
| FTP | FileTransferProtocol | This is used to transfer files | Transferring |
| from one host to another host | files | ||
| over a TCP-based network, | |||
| suchastheInternet. | |||
| HTTP | HyperTextTransfer | Define show messages are | WorldWide |
| Protocol | formatted and transmitted, | Web(www) | |
| and what actions Web | |||
| server sand browsers should | |||
| take in response to the wide | |||
| range of commands. | |||
| HTTPS | HyperTextTransfer | Provides authentication of | WorldWide |
| ProtocolSecure | the web site and associated | Web(www) | |
| web server andprotects | |||
| against man-in-the-middle | |||
| attacks. | |||
| VoIP | VoiceoverInternet | This enables people to use | Online |
| Protocol | the Internet as the | chat(thereare | |
| transmission medium for | exceptions) | ||
| telephone calls. | |||
Table 10- The Internet Protocols
The Internet uses a variety of languages to transmit information from one place to the other. These languages are called protocols. Using these protocols we can acquire the services from the Internet. Each protocol has a specific functionality and www is considered to be the largest service acquired amongst the services provided by the Internet.
Internet is an interconnection of computer networks all around the world. In other words, it is the hardware which forms the physical layer to these connections is what we refer to as the Internet. Hence, the Internet comprises of network of computers, fiber-optic cables, copper wires and wireless networks. But www is the software which is used to access the information from the Internet. It consists of files, folders and the documents which are stored in different computers. Now it is crystal clear to you that the www depends on the Internet to work.
Дата добавления: 2019-09-13; просмотров: 1005; Мы поможем в написании вашей работы! |

Мы поможем в написании ваших работ!
