Metropolitan Area Network (MAN)
MAN is a network that interconnect users with computer resources in a geographic area or region larger than that covered by a local area network (LAN) but smaller than the area covered by wide area network (WAN). Further a MAN is a network that connects two or more Local Area Networks or Campus Area Networks together but does not extend beyond the boundaries of the immediate town, city, or metropolitan area. See Figures 14,15 below for a typical set up of a MAN.
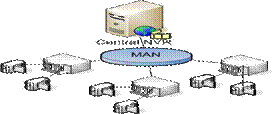
Figure 14- Metropolitan Area Network (MAN)

Figure 15- LAN, MAN, and WAN
Classifications of networks based on the topology
Network Topology is the schematic description how the arrangement of the network is including the nodes, connecting lines, and other devices. As per the above Table 7, the main network topologies are listed below.
- Bus
- Star
- Ring
- Mesh
- Tree/Hierarchical
Deep discussions on the topologies are beyond the level of this course unit. However, brief descriptions on each topology and images of them are given below.
Bus Topology
Bus networks (not to be confused with the system bus of a computer) use a common backbone to connect all devices. A single cable, the backbone, functions as a shared communication medium that devices attach or tap into with an interface connector. A device wanting to communicate with another device on the network sends a broadcast message onto the wire that all other devices see, but only the intended recipient actually accepts and processes the message.

Figure 16- Bus topology
Star Topology
Many home networks use the star topology. A star network features a central connection point called a "hub node" that may be a network hub, switch or router. Devices typically connect to the hub with Unshielded Twisted Pair (UTP) Ethernet.
Compared to the bus topology, a star network generally requires more cable, but a failure in any star network cable will only take down one computer's network access and not the entire LAN. (If the hub fails, however the entire network also fails.)
Ring Topology
In a ring network, every device has exactly two neighbors for communication purposes. All messages travel through a ring in the same direction (either "clockwise" or "counterclockwise"). A failure in any cable or device breaks the loop and can take down the entire network.
|
|
|

Figure 17- Star topology

Figure 18- Ring topology
To implement a ring network, one typically uses FDDI, SONET, or Token Ring technology. Ring topologies are found in some office buildings or school campuses.
Mesh Topology
Mesh topologies involve the concept of routes. Unlike each of the previous topologies, messages sent on a mesh network can take any of several possible paths from source to destination. (Recall that even in a ring, although two cable paths exist, messages can only travel in one direction.) Some WANs, most notably the Internet, employ mesh routing.
A mesh network in which every device connects to every other is called a full mesh. As shown in the illustration below, partial mesh networks also exist in which some devices connect only indirectly to others.

Figure 19- Mesh topology
Tree Topology
Tree topologies integrate multiple star topologies together onto a bus. In its simplest form, only hub devices connect directly to the tree bus and each hub functions as the root of a tree of devices. This bus/star hybrid approach supports future expandability of the network much better than a bus (limited in the number of devices due to the broadcast traffic it generates) or a star (limited by the number of hub connection points) alone.

Figure 20- Tree topology
The Internet
As you are already aware, the Internet is the largest WAN in existence (See Figure 21 below). It is a network of networks that consists of millions of private, public, academic, business, and government networks, of local to global scope, that are linked by a broad array of electronic, wireless and optical networking technologies. The Internet carries an extensive range of information resources and services, such as the inter-linked hypertext documents of the World Wide Web (WWW) and the infrastructure to support email.
With the dramatic rise in demand for connectivity, the Internet has become a communications highway for millions of users. The Internet was initially restricted to military and academic institutions, but now it is a full-fledged conduit for any and all forms of information and commerce. Internet websites now provide personal, educational, political and economic resources to every corner of the planet.
|
|
|

Figure 21- Internet: the largest WAN in existence
The Intranet and Extranet
The Intranet. You are already aware what the Internet is. Accordingly, the internet which is a worldwide system can be accessed by any person or by any organization. Since it is a vast public communication tool, some organizations were willing to maintain their own local network which supports their employees or the members. The Intranets were developed as a solution to the above requirement. However, the intranet also has almost all the services provided by the Internet, but it is a private system. The access of an intranet is restricted to the authorized members or people within the organization such that the authorized members need to log on with a secure password.
More comprehensively, intranets are private networks based on Internet Technologies that are located behind an organization‟s firewall. A Firewall is a set of technologies designed to protect a private network from users on a public network. Some intranets provide access to the Internet through a special server called a Proxy Server, designed to cache (to store for quick re-use) frequently requested information to keep that information readily available. This type of proxy server also provides tools for tracking and controlling access to networks.
An intranet can cover a LAN where only staff in the same building or region can use it. Or it can run over a WAN where staff (authorized people) from around the world can log in.
What Intranets do
Intranets usually start by publishing web pages about the organization‟s events, health and safety policies, and staff newsletters. Popular applications follow, such as forms to reclaim expenses or request holidays. All these help eliminate paperwork and speed up workflows of the organization.
As more features are added, this intranet can become essential to the operation of an organization. It becomes a portal that provides access to all the things workers need.
|
|
|
A typical intranet may provide the services such as E-mail, File transfer, Real time chat, web pages, video and audio streaming services. Each service requires at least one server to provide the service.
Advantages of an Intranet
· Commercial or confidential data is kept secured within the organization.
· E-mails remain private and may also be encrypted.
· High bandwidth. No connection limits unlike the Internet
· Reliable. The organization will have dedicated IT personnel to keep things running smoothly.
· Information specificity tailored to the organization or staff‟s needs can be published.
The Extranet
We can consider an Extranet as an extension to the Intranets what we described above. Because, the extranets are again private networks that contains information related to the company and accessible only for the members of the company BUT allowed for outside individuals as well who have obtained the authority to access. Therefore, an extranet is partially accessible to authorized outsiders.
An extranet can be configured (set up) either using a direct leased line linking all intranets or by using a secured separate link created across the participants as a VPN (Virtual Private Network). The latter method is more cost effective than the firs method.
Advantages of Extranets
- A cost effective method to share and trade information and all other data effectively at any time to the authorized people (internal and external) such as the customers, partners, investors, suppliers who are included within the built up extranet.
- A platform for companies to conduct business-to-business deals. Can assist in strengthening relationships between two or more organizations.
- Useful when the staff of the company works outside the office, from their homes, or sales sites so that they can still be in with the company network with the access permission.
4.DHCP protocol. Technologies of connection to the Internet.
|
|
|
Short for Dynamic Host Configuration Protocol, DHCP is a protocol used to assign an IP address to a computer or device that has been connected to a network automatically. Routers, switches, or servers that use DHCP to assign addresses to other computers can make setup and management easier for the network administrator.
On a home network, DHCP can be setup by purchasing a home router, wireless router, or switch with NAT/DHCP and connecting each computer to it. If the network has a firewall, ports 67 and 68 need to be open for devices to function properly.
Configuring a DHCP Server
To configure a DHCP server, you must create the dhcpd.conf configuration file in the /etc/ directory. A sample file can be found at /usr/share/doc/dhcp-<version>/dhcpd.conf.sample.
DHCP also uses the file /var/lib/dhcpd/dhcpd.leases to store the client lease database.
Configuration File
The first step in configuring a DHCP server is to create the configuration file that stores the network information for the clients.Use this file to declare options and global options for client systems.
The configuration file can contain extra tabs or blank lines for easier formatting. Keywords are case-insensitive and lines beginning with a hash mark (#) are considered comments.
Two DNS update schemes are currently implemented — the ad-hoc DNS update mode and the interim DHCP-DNS interaction draft update mode. If and when these two are accepted as part of the Internet Engineering Task Force (IETF) standards process, there will be a third mode — the standard DNS update method. You must configure the DNS server for compatibility with these schemes. Version 3.0b2pl11 and previous versions used the ad-hoc mode; however, it has been deprecated. To keep the same behavior, add the following line to the top of the configuration file:
ddns-update-style ad-hoc;To use the recommended mode, add the following line to the top of the configuration file:
ddns-update-style interim;Refer to the dhcpd.conf man page for details about the different modes.
There are two types of statements in the configuration file:
· Parameters — State how to perform a task, whether to perform a task, or what network configuration options to send to the client.
· Declarations — Describe the topology of the network, describe the clients, provide addresses for the clients, or apply a group of parameters to a group of declarations.
The parameters that start with the keyword option are reffered to as options. These options control DHCP options; whereas, parameters configure values that are not optional or control how the DHCP server behaves.
Parameters (including options) declared before a section enclosed in curly brackets ({ }) are considered global parameters. Global parameters apply to all the sections below it.
Important
If the configuration file is changed, the changes do not take effect until the DHCP daemon is restarted with the command service dhcpd restart.
Tip
Instead of changing a DHCP configuration file and restarting the service each time, using the omshell command provides an interactive way to connect to, query, and change the configuration of a DHCP server. By using omshell, all changes can be made while the server is running. For more information on omshell, refer to the omshell man page.
Additionally, a subnet can be declared, a subnet declaration must be included for every subnet in the network. If it is not, the DHCP server fails to start.
In this example, there are global options for every DHCP client in the subnet and a range declared. Clients are assigned an IP address within the range.
Lease Database
On the DHCP server, the file /var/lib/dhcpd/dhcpd.leases stores the DHCP client lease database. Do not change this file. DHCP lease information for each recently assigned IP address is automatically stored in the lease database. The information includes the length of the lease, to whom the IP address has been assigned, the start and end dates for the lease, and the MAC address of the network interface card that was used to retrieve the lease.
All times in the lease database are in Coordinated Universal Time (UTC), not local time.
The lease database is recreated from time to time so that it is not too large. First, all known leases are saved in a temporary lease database. The dhcpd.leases file is renamed dhcpd.leases~ and the temporary lease database is written to dhcpd.leases.
The DHCP daemon could be killed or the system could crash after the lease database has been renamed to the backup file but before the new file has been written. If this happens, the dhcpd.leases file does not exist, but it is required to start the service. Do not create a new lease file. If you do, all old leases are lost which causes many problems. The correct solution is to rename the dhcpd.leases~ backup file to dhcpd.leases and then start the daemon.
Дата добавления: 2018-11-24; просмотров: 537; Мы поможем в написании вашей работы! |

Мы поможем в написании ваших работ!
